How to store your Microsoft FSLogix Profile Container on Azure Files with Azure Active Directory Domain Services (AADDS) as platform service for Azure Virtual Desktop
Success in the Cloud relies on the automated infrastructure and leveraging as much as platform-as-a-service (PaaS) services, such us Azure Files – the native Azure storage platform service that I handle in this article. The Cloud is definitely not about lifting and shifting to Infrastructure-as-a-Services – it must save management and maintenance effort as well as eventually benefit in costs.
“DOS is fundamental for Windows, and Windows will be the fundament for Microsoft Azure.” – This quote reminds me of how fast we are going to leverage Azure Cloud Platform Services, such as Azure Files. – Christiaan Brinkhoff
This article focuses on Azure Virtual Desktop, however, it also applies to every virtual desktop workload that is running on Azure. Use it for your own advantage to leverage the benefits of your Azure storage account.
Are you looking for the same manual for native Active Directory instead of Azure Active Directory Domain Services (AADDS). Please visit one of my other articles here.
Table of Contents
Click on the title to jump to that spot in this article:
- Differences between IaaS and PaaS
- Differences between (current and previous) Microsoft user profile solutions
- Pre-step: How to enroll in Azure Active Directory Domain Services
- Pre-step: Create an Azure storage account
- How to enable Azure Files for Azure AD Domain Services w/ ACLs?
- Create or select Azure Storage Account
- Verify appropriate network configuration
- Add an Azure files share
- Configure Azure Files Azure Active Directory Authentication for SMB
- Enable Azure Active Directory Authentication
- Define Share Level User Permissions
- Configure NTFS Permissions
- Verify Configuration
- Configure FSLogix Profile Container
Did you know?
- Azure file shares support the industry standard SMB protocol, meaning you can seamlessly replace your on-premises file shares with Azure file shares without worrying about application compatibility. Being able to share a file system across multiple machines, applications/instances is a significant advantage with Azure Files for applications that need shareability.
- Azure Files makes it easy to “lift and shift” applications to the cloud that expect a file share to store file application or user data. Azure Files enables both the “classic” lift and shift scenario, where both the application and its data are moved to Azure, and the “hybrid” lift and shift scenario, where the application data is moved to Azure Files, and the application continues to run on-premises.
- Azure Files permissions should match permissions described in Requirements – Profile Containers.
- Each host pool must be built of the same type and size VM based on the same master image.
- Each host pool VM must be in the same resource group to aid management, scaling and updating.
- For optimal performance, the storage solution and the FSLogix profile container should be in the same data center location.
- The storage account containing the master image must be in the same region and subscription where the VMs are being provisioned.
- Azure file shares can be created without the need to manage hardware or an OS. This means you don’t have to deal with patching the server OS with critical security upgrades or replacing faulty hard disks.
- PowerShell cmdlets and Azure CLI can be used to create, mount, and manage Azure file shares as part of the administration of Azure applications.You can create and manage Azure file shares using Azure portal and Azure Storage Explorer.
- Azure Files has been built from the ground up to be always available. Replacing on-premises file shares with Azure Files means you no longer have to wake up to deal with local power outages or network issues.
- Applications running in Azure can access data in the share via file system I/O APIs. Developers can, therefore, leverage their existing code and skills to migrate existing applications
Differences between IaaS and PaaS
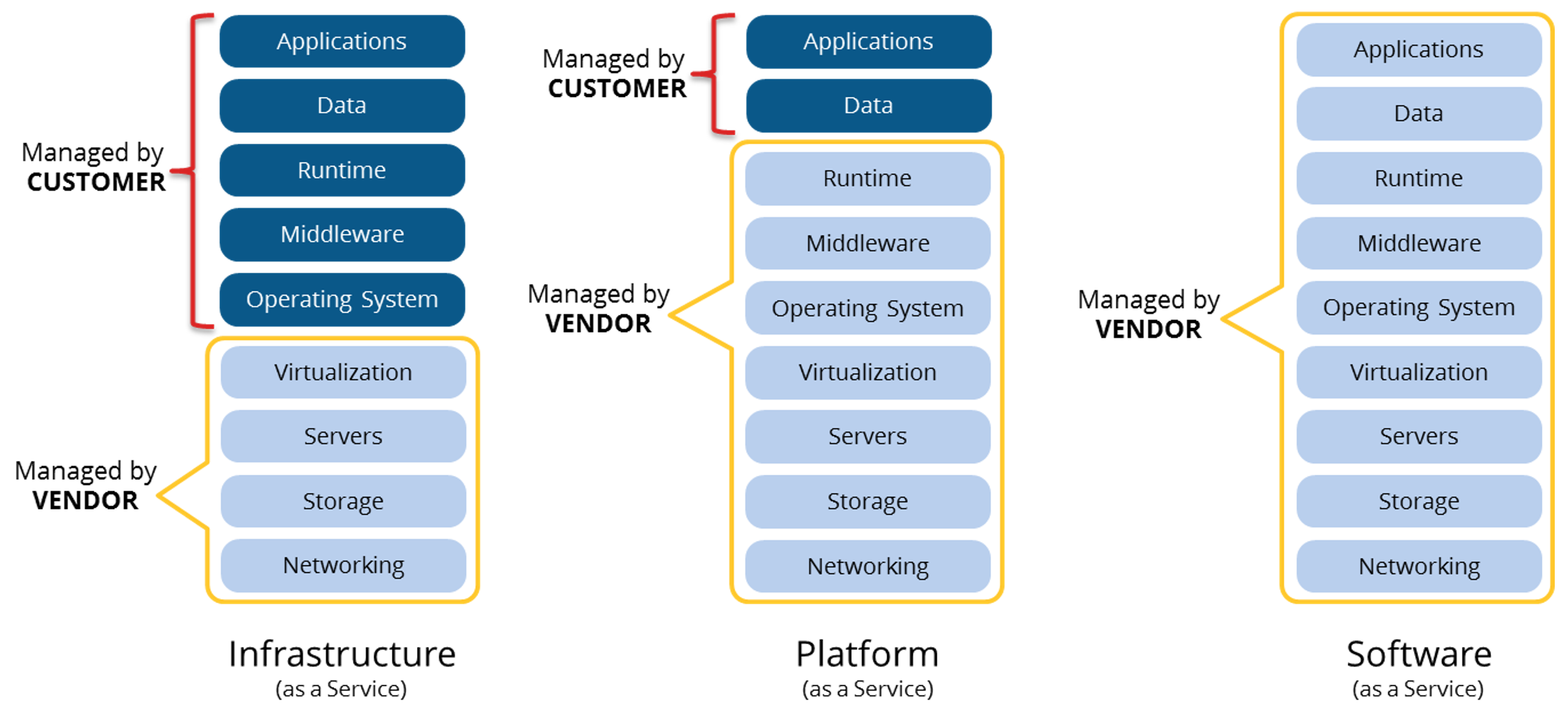
As I mentioned at the beginning of this article, success in the Cloud relies on automated infrastructure and leveraging platform services. This resonates in some heads, however, not everyone is aware of the differences between Infrastructure-as-a-Service(IaaS), Platform-as-a-Service (PaaS)and Software-as-a-Service (SaaS) – services on the public cloud – all based on an OpEx billing payment structure.
IaaS is releasing you from hypervisor and storage management. All the other tasks are still your responsibility. This is the most common situation, which is also called Lift-and-Shift. Not the most ideal migration method, however, sometimes the best one for a certain amount of time to switch over to PaaS or SaaS.
With PaaS, you’re sharing the same resources with others, which makes it more affordable to use. The server itself runs on Azure and is managed and maintained by Microsoft. Your uptime and performance is guaranteed with an SLA.
When we talk about Desktop-as-a-Service solutions, such as Azure Virtual Desktop – the applications and Data is image management as a replacement for section two. All the other parts are management by Microsoft. Get to know more about that here.
Software-as-a-Service is the simplest (and obvious) one to explain. No responsibility what so ever – everything is managed and maintained by the Cloud vendor.
Differences between (current and previous) Microsoft user profile solutions
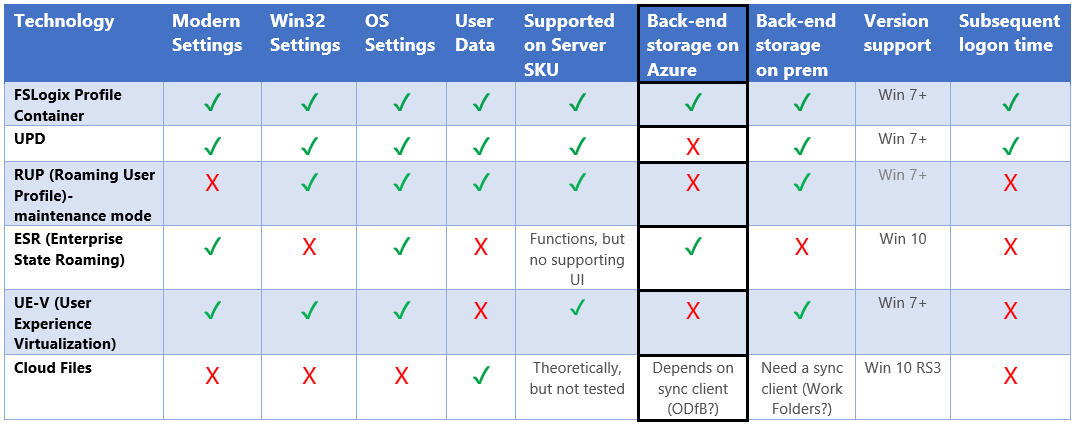
None of the existing Microsoft user profile solutions is capable of handling all needs that come up in and RDSH / VDI environment. UPD could not handle large OST files. RUP was not persisting modern setting. The table below is a good summary of existing and missing capabilities around user profile technologies. I’ve added FSLogix profiles to the solutions matrix which I shared earlier this week on my socials.
Keep in mind that the Profile Container is Microsoft’s recommended solution for all environments with non-persistent profiles. UPD will be depreciated in the near future and replaced by Profile Container.
I’ve also highlighted the Back-end storage on Azure part of this matrix due to the fact that this article is completely based on this use-case! 🙂
Note: Please read this official Microsoft Docs article from Stefan Georgiev around FSLogix and Azure Files best practices as follow up to this article.
What is Azure AD Domain Services
We all know (classic) Active Directory, right? Running DCPROMO and building the forest yourself. Azure Active Directory is the next step while leveraging different Azure services. However, due to compatibility reasons, it could be that you still need to use a classic Active Directory domain. For example, you may need to join your computer or server to a domain in order to support a Win32 application you’re running in Azure.
Azure Active Directory Domain Services makes it possible to join your virtual machines to a classic AD domain, without having to deploy domain controllers in Azure Infrastructure-as-a-Service. This saves you costs and management effort as well. Yes, you get me here. This is a Platform-as-a-Service version of Active Directory for the lowest TCO in Azure.
Azure Files with ACLs (NTFS) right support (preview)
Azure Files offers fully managed file shares in the cloud that are accessible via the industry standard SMB protocol. Integration with AAD enables SMB access to Azure file shares using AAD credentials from AAD DS domain-joined Windows VMs. In addition, Azure Files supports preserving, inheriting, and enforcing Microsoft file system NTFS ACLs on all folders and files in a file share (in preview). This can be used to replace the need for a file server (cluster) for your user and/or FSLogix Profile Container data (as well for applications that require an SMB share to work).
Azure Files enforces standard NTFS file permission on the folder and file level, including the root directory. You can simply use the icacls or Powershell command tool to set or change permissions over mounted file shares.
You could leverage this Azure service to store your Azure Virtual Desktop Profiles in for the lowest TCO possible because you don’t have to run the SMB share on a dedicated VM storage instance, such as Storage Spaces Direct.
Continue reading, I explain all the technical details later on
Azure Files Performance configuration differences
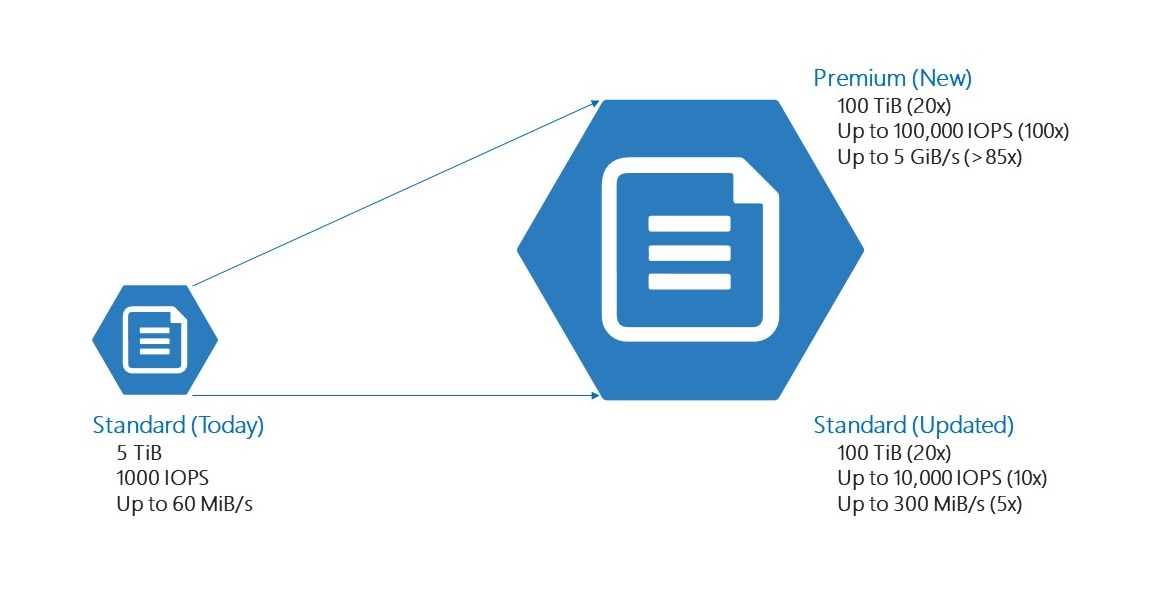
Standard files, our existing storage, is designed to provide reliable performance for IO workloads that are less sensitive to performance variability. It is well suited for general purpose files services and dev/test environments. We have also made significant investments in standard files to increase the capacity limits by 20x and IOPS limits up to 10x.
Premium Files, preferred for the use of Profile Containers, is optimized to deliver consistent performance for IO-intensive enterprise workloads that require high throughput with single digit millisecond latency. Premium Files is suitable for a wide variety of workloads such as databases, home directories, analytics, content, and collaboration. Its performance, whether measured by IOPS or throughput, scales with the provisioned capacity to fit your workload’s needs. With premium file shares, IOPS can scale up to 100x and capacity can scale up to 20x the current Azure Files scale limits.
Going Hybrid? Think about Azure Files Sync
Azure Files is maybe a step too soon for your environment. This can be multiple reasons, the most obvious one it due to latency and distance because your applications are still living in a private cloud datacenter. For this sake, Azure Files Sync can help you. It uses the same Azure Files service with the possibility to place the data near your servers in your own datacenter through a so-called endpoint server. It also supports DFS to assign the new storage location to your existing universal namespace.
The cool thing is that you can manage your hot and cold data as well. You can replicate your hot physical data to your servers, whereby the cold data doesn’t replicate to the endpoint – but is available and start downloading the file while clicking on it. It’s a similar process to OneDrive Files On-Demand.
Read more about this in one of my previous articles below.
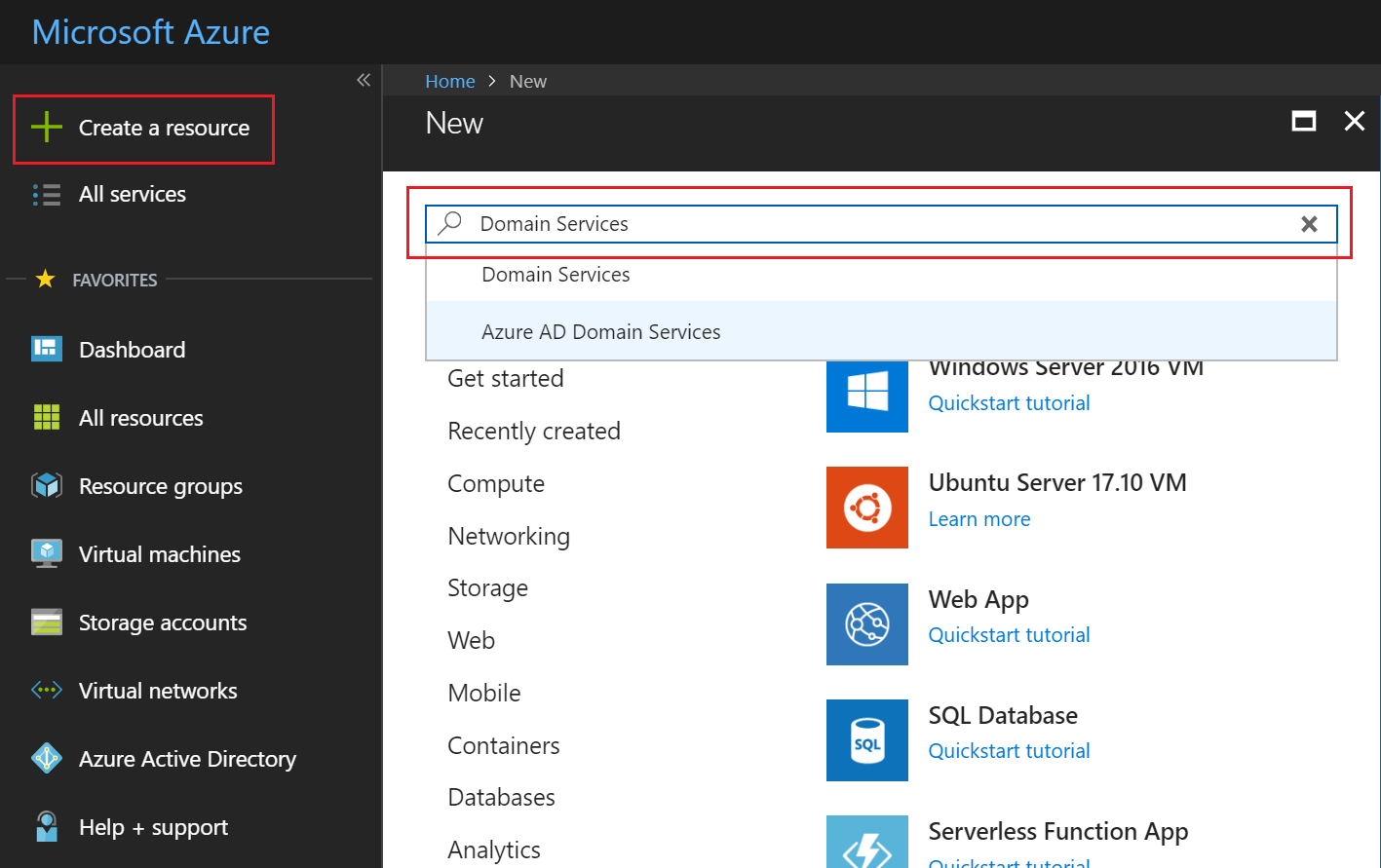
Pre-step: How to enroll in Azure Active Directory Domain Services
The enrollment process of Azure Active Directory is very easy and simplified as you would expect from a platform service. The Microsoft Docs article below describes in a comprehensive way how to get started with the Azure service.
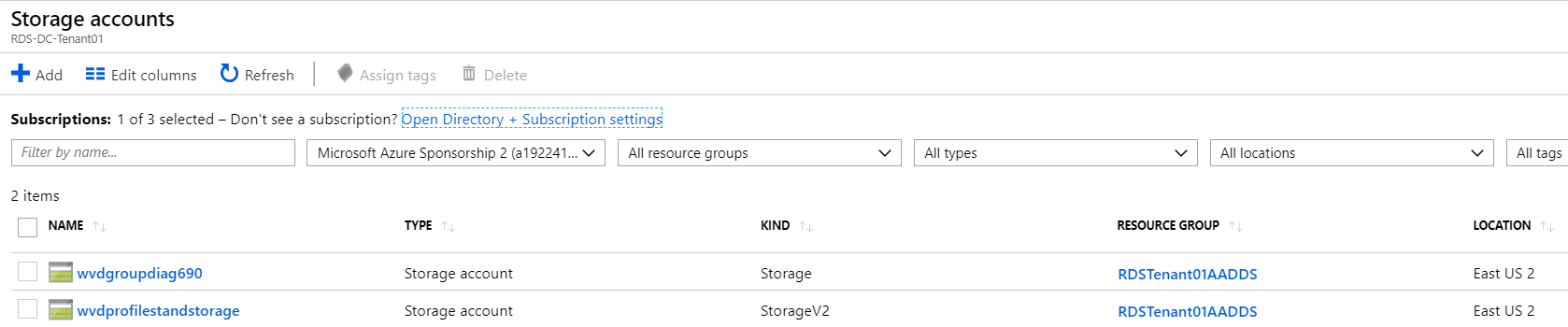
Create or select Azure Storage Account
Open Storage accounts in your Azure Portal and create a Storage Account.
Or perform the following PowerShell Command instead.
New-AzStorageAccount -ResourceGroupName "<resource-group-name>" ` -Name "<storage-account-name>" ` -Location "<azure-region>" ` -SkuName Standard_LRS ` -Kind StorageV2 ` -EnableAzureFilesAadIntegrationForSMB $true
Add a file share
Create an SMB share in the Azure Files section. This can be a random name.
Configure Azure Files Azure Active Directory Authentication for SMB
Now we must enable the – Azure Active Directory authentication for Azure Files (Preview) – feature, which can be found at the Configuration menu within your Storage account.
Note: This setting is already enabled when you use the PowerShell command to create the storage account.
Define Share Level User Permissions
To perform the rights to our Azure Files share, we must first install the Azure Storage PowerShell module. This can be done via the command below.
Note: You need to have at least PowerShell v5.1 to run the command. If the command fails, please run this Install-Module PowershellGet -Force command first. Another alternative is to import the module manually. Az.Storage preview files can be found here.
Install-Module -Name Az.Storage -AllowPrerelease -Force -AllowClobber
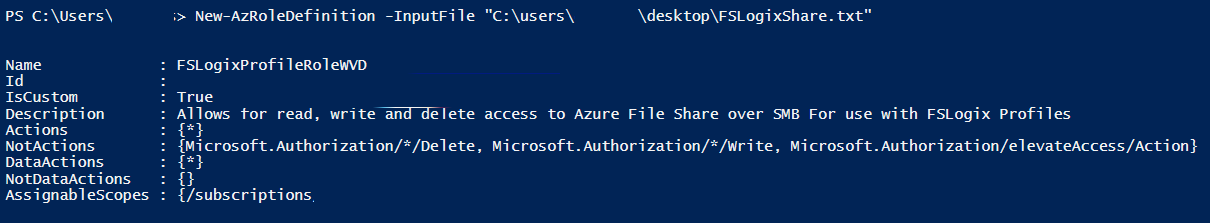
Now you need to define a custom role. Remove the <Custom-Role-Name> and make it your own.
Save the JSON file somewhere on your C:\ drive and continue with the next step.
{
"Name": "<Custom-Role-Name>",
"Id": null,
"IsCustom": true,
"Description": "Allows for read, write and delete access to Azure File Share over SMB",
"Actions": [
"*"
],
"NotActions": [
"Microsoft.Authorization/*/Delete",
"Microsoft.Authorization/*/Write",
"Microsoft.Authorization/elevateAccess/Action"
],
"DataActions": [
"*"
],
"AssignableScopes": [
"/subscriptions/<Subscription-ID>"
]
}
Create the custom role from the JSON / or .txt file as a source.
New-AzRoleDefinition -InputFile "Path to JSON or TXT file"
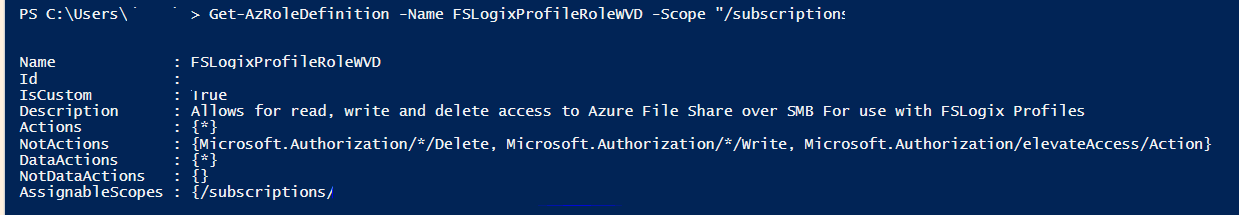
Verify the custom role was created (NOTE: If you have multiple subscriptions you must specify ID)
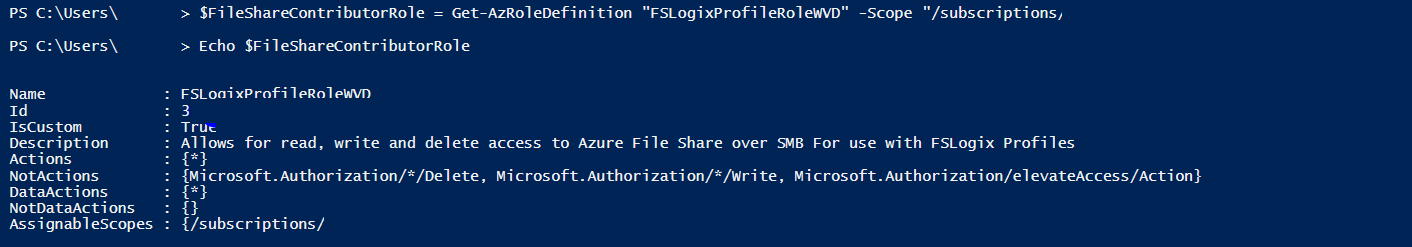
Create a structure with role definition and verify the success
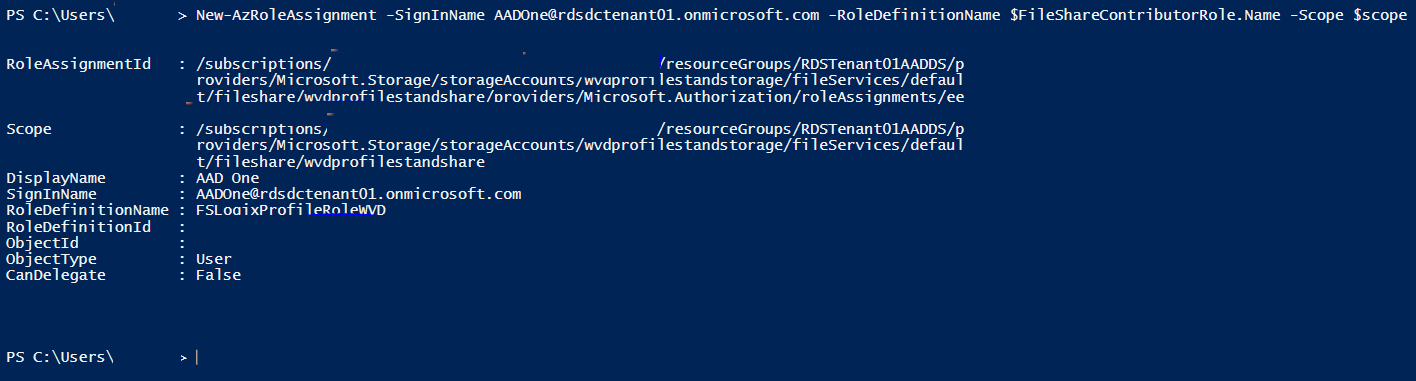
Create “scope” structure for use when assigning users to Role…
Create Role Assignment
Assign the NTFS Permissions
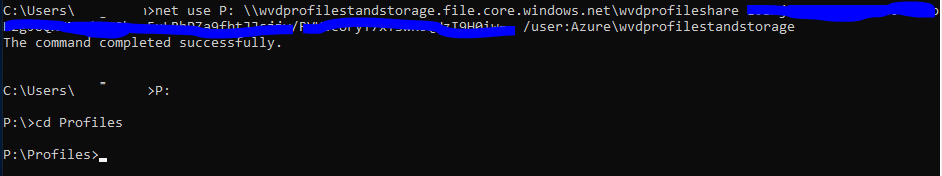
Mount Store using Storage Account and Share ID
net use <desired-drive-letter>: \\<storage-account-name>.file.core.windows.net\<share-name> <storage-account-key> /user:Azure\<storage-account-name>
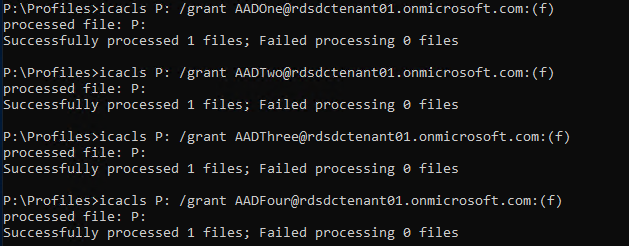
Grant Appropriate User Permissions using icacls or Set-ACLS (for Preview File Explorer shows permissions but cannot be set)
icacls <mounted-drive-letter>: /grant <user-email>:(f)
This process is for use with Preview, instructions / Process will likely evolve as Azure AD Authentication moves towards GA…
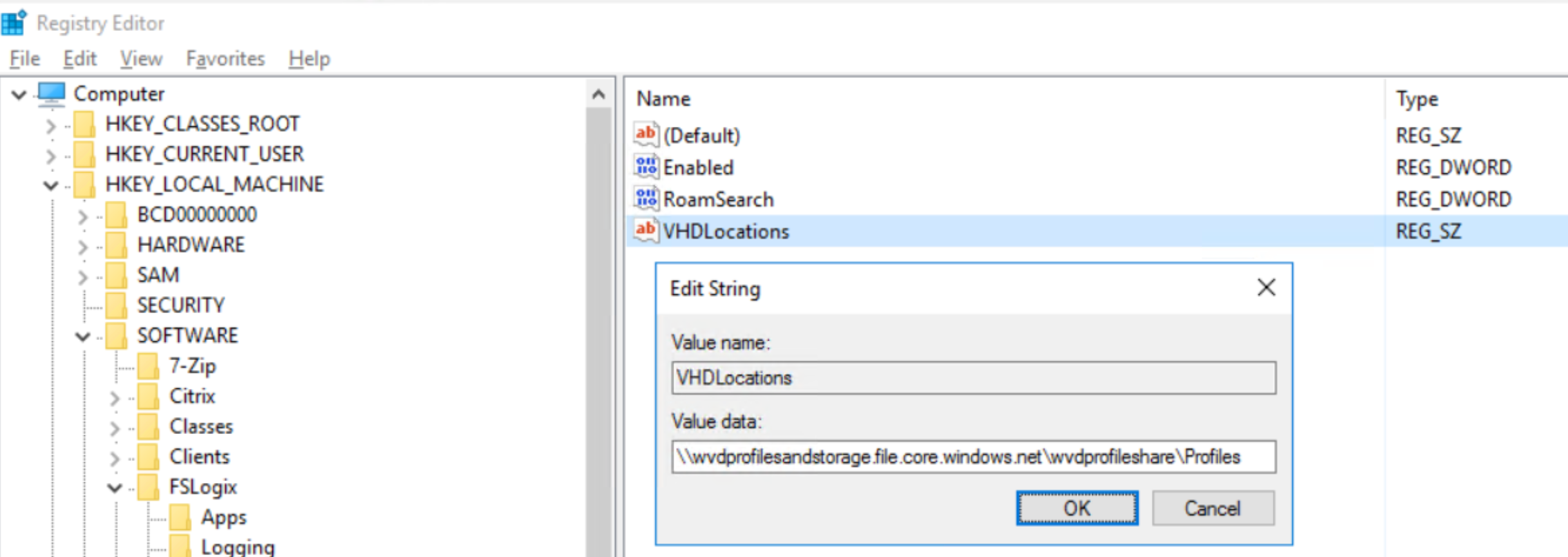
Configure FSLogix Profile Container for Azure Files
Make sure to use the public storage account URI followed by the share location you created. The rest of the settings can be let default. Azure AD will now proceed with access through the right you defined as part of the ACLs.
Hope this helps to get familiar with Azure Files. There are updates coming to this feature, which results in more and more interesting use-cases for your customers. Stay tuned.
Some follow up links that you might want to read
- https://www.christiaanbrinkhoff.com/2019/03/21/the-future-of-roaming-profiles-add-fast-logon-performance-and-office-365-support-to-your-virtual-desktop-vdi-daas-environment-with-microsoft-fslogix-profile-container-including-existing-uem-sol/
- https://docs.microsoft.com/en-us/azure/storage/files/storage-files-active-directory-overview
- https://docs.microsoft.com/en-us/azure/storage/files/storage-files-active-directory-enable
- https://docs.microsoft.com/en-us/azure/active-directory-domain-services/active-directory-ds-overview
- https://docs.microsoft.com/en-us/azure/active-directory-domain-services/active-directory-ds-admin-guide-administer-group-policy
Cheers,
Christiaan Brinkhoff