Activate Azure AD Bring-Your-Own-Identity authentication for the Citrix Workspace Experience unified portal, including Conditional Access configuration
Imagine how it would be to have one unified entry-point as well as the same identity for all your Cloud, SaaS, Web Apps or on-premises (published) applications. How awesome would it be to use a mobile device as authentication instead off all the sloppy and insecure password you used (and probably still use) throughout the past years?
“One authentication method to rule them all” – Christiaan Brinkhoff
We – IT Professionals, or better say Cloud Consultants will help businesses to leverage their on-premises environment to migrate to the Cloud – first optimize business processes to replace them by Cloud services to take full advantage of the simplicity and cost savings of the Public Cloud, such as Microsoft Azure. Lift and Shifting is some of those approaches that you want to avoid, it’s very costs effective, and that’s not where the main profit can be reached on a Cloud perspective! The Cloud also brings a better mechanism to access your resources. Don’t you remember users that are complaining about different passwords, applications and authentication methods? They can’t have been managed them all by themselves, so we need to help them to simplify this procedure!
Citrix is doing a good job on solving this problem with the new Citrix Workspace Experience from inside the Citrix Cloud. Use this new approach of your workspaces combined with Azure MFA and Conditional Access and your security will increase. Don’t you think that some users in your environment are having too easy password to guess for hack attempts? You can’t prove it, but you know some are… With Azure MFA you can lower that risks, which’ll eventually exceed the security level and make you feel more confident about the user security level of your environment.
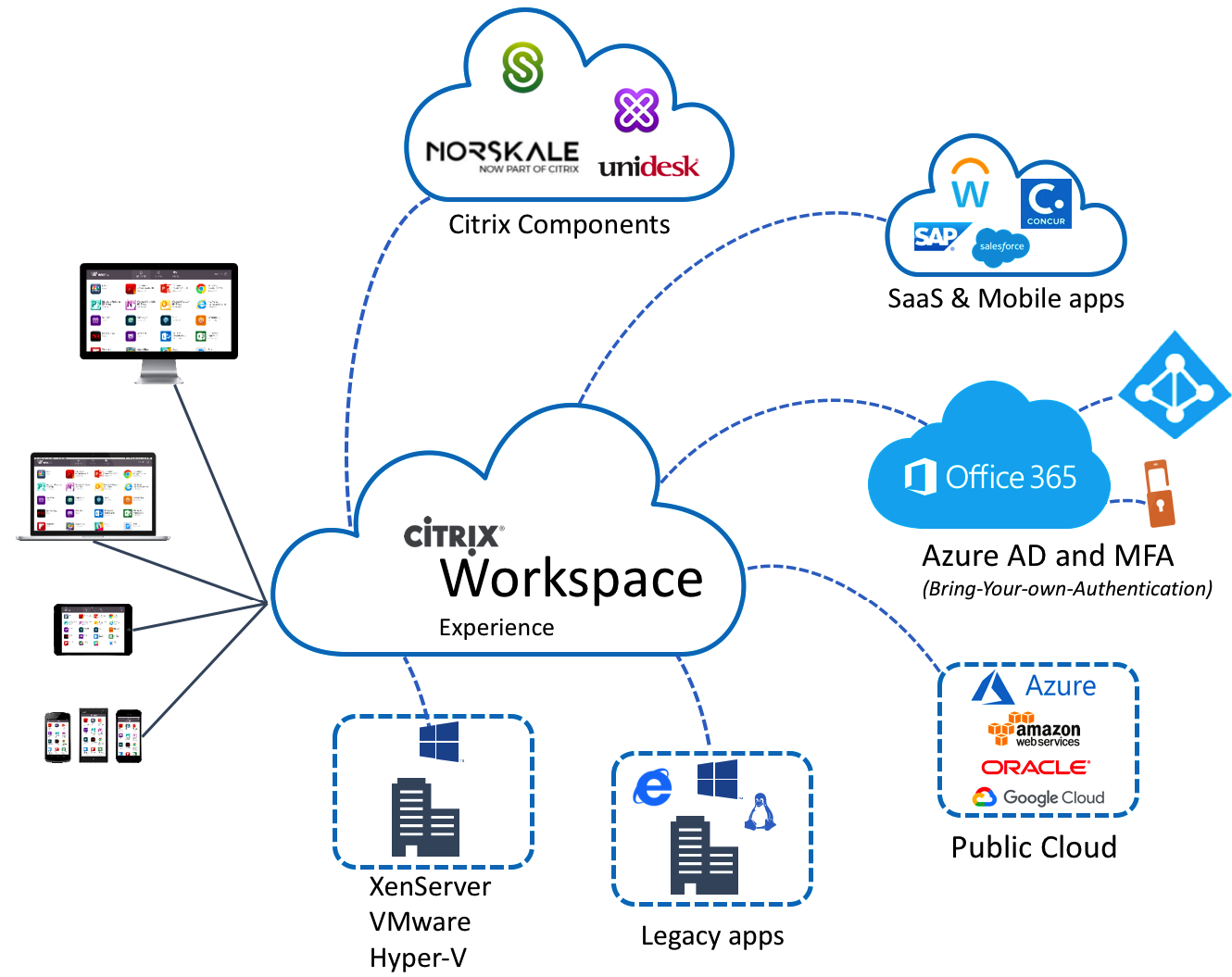
Personally, I’m very excited about the Citrix Workspace Experience. This new unified portal, which’ll gives the end-user the same experience for all their Apps and Desktops through one single pane of glass is very useful for Cloud transitions. Whether it’s a Cloud web app, on-premises Published Apps from a XenApp 6.x or 7.x platform, or just a Full Desktop in the Microsoft Azure Cloud – the end-user could use them all in the same HTML5 enabled browser with a SSO (Single-Sign-On) experience, how cool is that?!
Citrix is going to release a huge upgrade on Workspace Experience during Synergy, so stay tuned!
The following drawing shows how all the Citrix Workspace components come all together in one single pain of glass – unified portal in Workspace Experience.
In this article, I’ll show you how you can use the Citrix Workspace (Experience) Unified Portal activated with Azure Active Directory authentication, including the extra Azure Multi-Factor security layer. You’ll also find some tips around Conditional Access at the end of this article and a small demo video.
Are you going to Synergy and want to know more about the Citrix Workspace Experience? I encourage you to go to see the SYN239 From StoreFront to Citrix Workspace session of Hoe Vaccaro and Craig Hinchliffe! And of course, the SYN105 session of me and George Kuruvilla about Deploying Citrix Workloads on different clouds: CTP best practices for a successful deployment!
Note: Searching for Azure MFA for NetScaler in a on-premises scenario? Please check one of my previous blog articles for a comprehensive walk through.
Enjoy reading!
Table of contents
Click on the title to get forwarded in the article:
- Enable Azure MFA in the Azure Portal
- Connect the Citrix Cloud to AzureAD
- Activate Azure AD Workspace Authentication
- Demo – see it yourself
More on Digital Workspaces in Azure?
This blog is part of a Citrix Cloud blog series about the different Citrix Cloud Digital Workspaces possibilities. Previous articles that I wrote around the Citrix Cloud, that you might find interesting to read:
- How to configure the Enlightened Data Transport UDP Protocol (EDT) when using the Citrix Cloud – XenApp and XenDesktop Service with the VDA and NetScaler placed in the Microsoft Azure Cloud
- How to configure Citrix Cloud – App Layering 4.8 to deliver virtualized apps and Office 365 caching – User Layers for XenApp and XenDesktop Service Cloud Workspaces in Microsoft Azure
- How to configure the Citrix Cloud XenApp and XenDesktop Service using Azure Managed Disks and Citrix Optimizer
- How to configure Citrix XenApp Essentials in Microsoft Azure, including Azure Active Directory authentication to Citrix Cloud
- How to use Citrix Smart Tools – Smart Scale to reduce your XenApp and XenDesktop on Azure Cloud resource costs
- How to configure a Bring-your-Own NetScaler VPX in Azure for XenDesktop Essentials and XenApp and XenDesktop Service from the Citrix Cloud
- How to configure Azure Active Directory Domain Services for Citrix Cloud Workspaces with the lowest Total-Cost-of-Ownership in Azure Infrastructure-as-a-Service
Did you know these facts?
-
- For Azure MFA to work, your Active Directory must be synchronized with an Office 365 account through Azure AD Connect.
- You can also use Azure AD Domain Services to replace the normal Active Directory by Active Directory-As-a-Service within Azure. Interested? See one of my previous blogs how to implement it.
- MFA is an easy way to protect your workspace environment as extra layer upon the “easy to guess” user passwords.
- You could use the Mobile Phone – Authenticator App to approve the request, therefore Mobile Phone Call and SMS texts are also supported!
- The new Unified Portal can only be used from inside the Citrix Cloud, therefore it supports resource locations in almost every Public Cloud resource location, also on-premises locations!
- You could also use the Citrix Cloud Connector to on-premises resource locations, which makes it very flexible in during a transition phase to the Cloud.
- It aligns with all the other Azure / Office 365 services, such as ShareFile, Exchange, Office365 and SharePoint.
- Citrix Workspace Experience also supports the configuration through the Local Citrix Receiver software and mobile apps, which allows you to add shortcuts in the start menu for published apps and desktops.
- Single Sign On from the Workspace Experience portal to your Desktops and Published Apps as well is not yet supported when u use the Azure AD (tech preview) authentication feature. The technical reason for this is that Citrix Workspace Exp. is not yet supported for FAS integration with Microsoft Azure AD, this is the technical reason why there is no authentication pass-through possible…
- XenApp Essentials and XenApp Service now also supports Published Desktops (multi-sessions)?
- You’ll need an Azure AD Premium or the EMS License activate to a AzureAD user for activating MFA. Note: If you don’t have those license, please purchase and activate them before you proceed steps that you can find in this article.
- There is also a possibility to use Azure MFA for on-premises authentication, such as NetScaler. You’ll need one of the 2 methods for providing this:
- 1: Using the server less MFA NPS extension + Azure AD Connect
- 2: Install the local MFA server + Azure AD Connect
- With Azure AD, you’ll have lots of possibilities of Microsoft Azure, all delivers from one identity provider. Learn more about conditional access later on in this article.
- For Azure MFA to work, your Active Directory must be synchronized with an Office 365 account through Azure AD Connect.
Note: Citrix will release some great improvements around the Citrix Workspace Experience during Synergy in May. So stay tuned on my socials during the event!
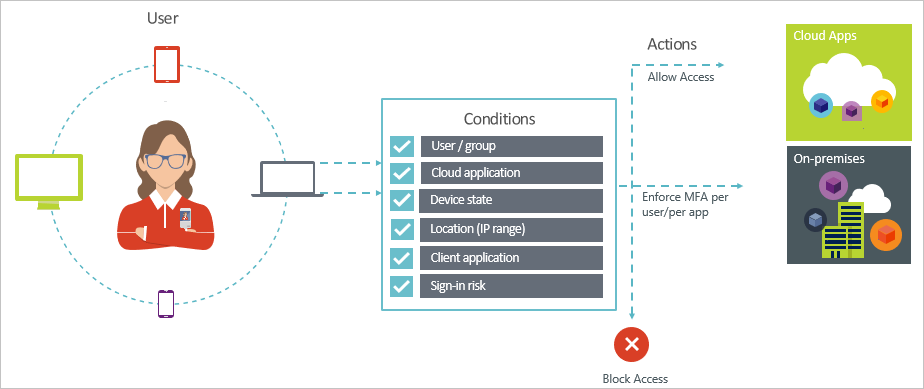
Conditional Access
Azure MFA is something that needs to be turned-on by default when u use Azure Active Directory. In a security perspective, it is the best way to ensure that the account isn’t accessible by hackers – or other people that are willing to take advantage of a user account. I’m still seeing a lot of users with passwords, such a Welcome2018 or QWERTY2018. To increase the authentication security level of your environment, I’d recommend you to add Azure MFA as extra sec. layer.
Most of the users are complaining about those extra steps. They don’t see it from a security perspective and have no understanding why it’s required to add these steps. By using conditional access policies, you can apply the right access controls under the required conditions. Azure AD conditional access provides you with added security when needed and stays out of your user’s way when it isn’t. For instance, you can exclude external subnets to avoid that people need to use MFA in their internal network.
Note: Need to know more about Azure Conditional Access? Please read this Microsoft Docs article.
Common use cases for this condition are policies that:
- Require multi-factor authentication for users accessing a service when they are off the corporate network.
- Block access for users accessing a service from specific countries or regions.
I’ll cover the Multi-Factor authentication IP whitelisting part later on in this article.
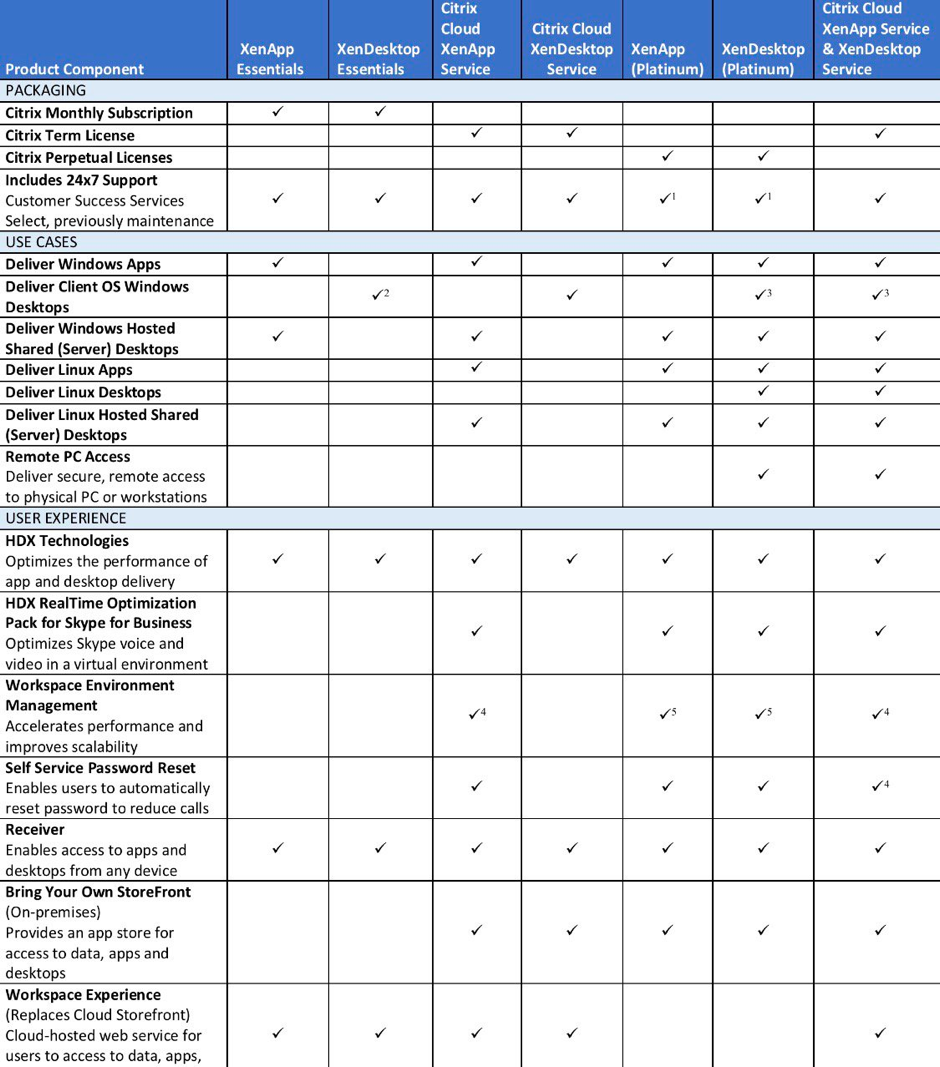
Workspace Comparison Cheat sheet
Citrix just released a new comprehensive version of the Citrix Workspaces comparison sheet where they gathered all the information that you’ll need to know when u choosing for Citrix in the Cloud or just on-premises.
See the complete sheet here
XenApp Essentials in Azure supports Published Desktops
I’ve been (and my customers) waiting for this feature for a very long time. As you probably know, since the release of XenApp Essentials, it was only possible to provide Published Apps. For 2 weeks, Citrix changed that opened a lot of new doors for potential new Citrix customers in the Microsoft Azure Cloud.
Note: XenApp Essentials also supports the Workspace Experience, including AzureAD and MFA authentication.
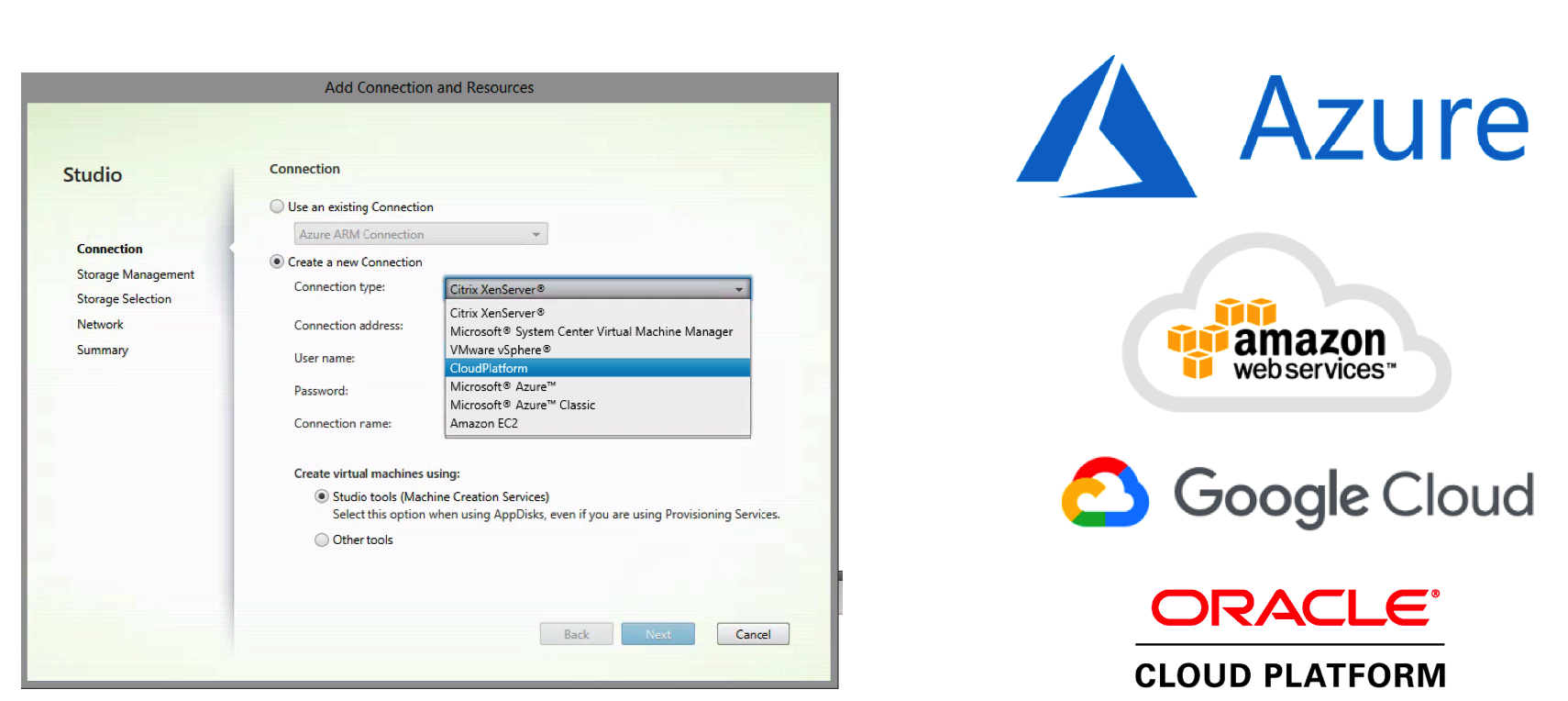
Multi-Cloud support
Multi-Cloud has been some of the strategies of Citrix that results in the support for different cloud from almost day one, and they’re still expanding their support for different Cloud vendors. therefore, it’s still confusion which Could will be the best fit for your organization. We usually agree on is that it says something about mixing and combining the best technologies and services from different cloud providers to create the best possible solution for a particular organization and/or ‘ workload ‘. Keep in mind that the Multi-Cloud support is only possible with the XenApp and XenDesktop Service, XenApp Service & XenDesktop Service as well as the on-premises versions.
During the Host Connection setup, you’ll get the change to connect to the following Cloud platforms, which you can see in the picture below.
Enable Azure MFA in the Azure Portal
Before you start: I assume that you already have an on-premises environment with Azure AD Connection configured, this is needed to provide the next steps. To enable the MFA functionality for your Azure AD users you first need to but Azure MFA or Azure AD Premium licenses within the portal.office.com – Office 365 license portal, otherwise you’ll get problems with the next steps!
Note: you also could use Azure MFA without the need for a Active Directory server on-premises or in Azure IaaS, by replacing them for the Azure AD Domain Services feature. Interested? Check out one of my previous blogs.
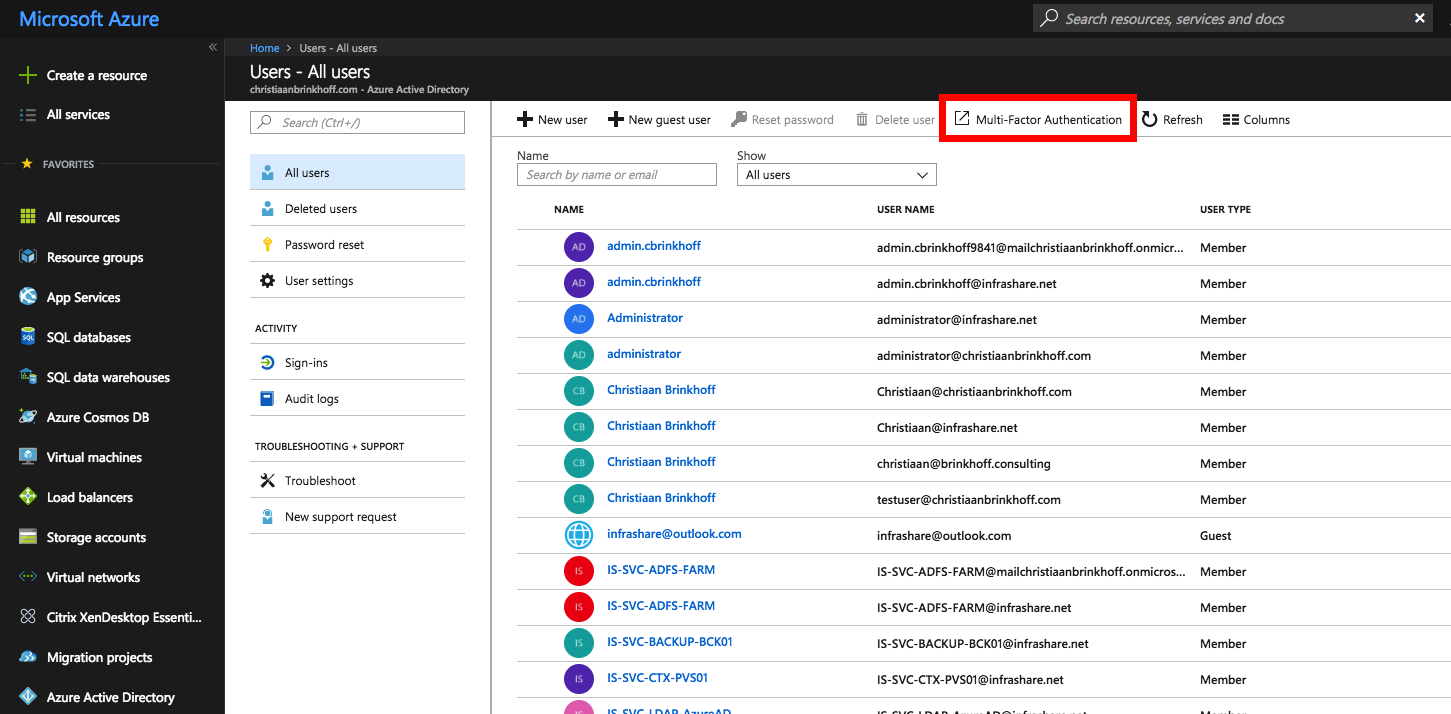
Go to portal.azure.com
Go to Azure Active Directory in the Services menu

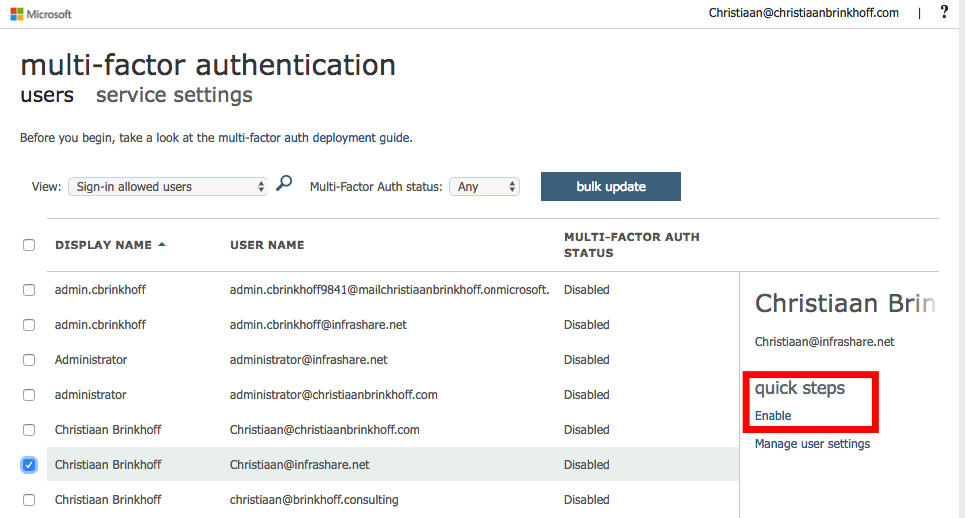
Click on Multi-Factor Authentication
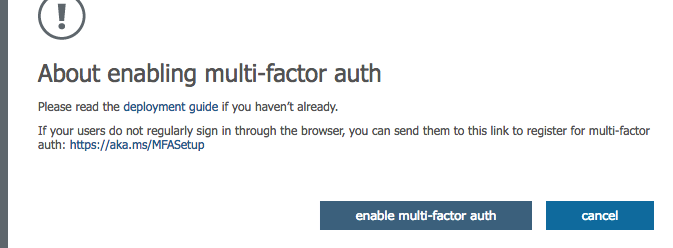
Enable MFA for every user in your environment
Click on enable multi-factor auth
Connect the Citrix Cloud to AzureAD
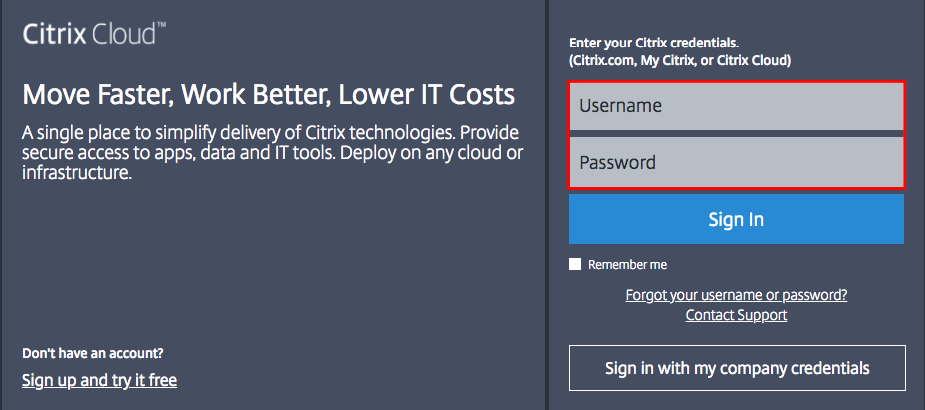
Go to citrix.cloud.com
Enter in the Citrix Cloud credentials
click on Sign In
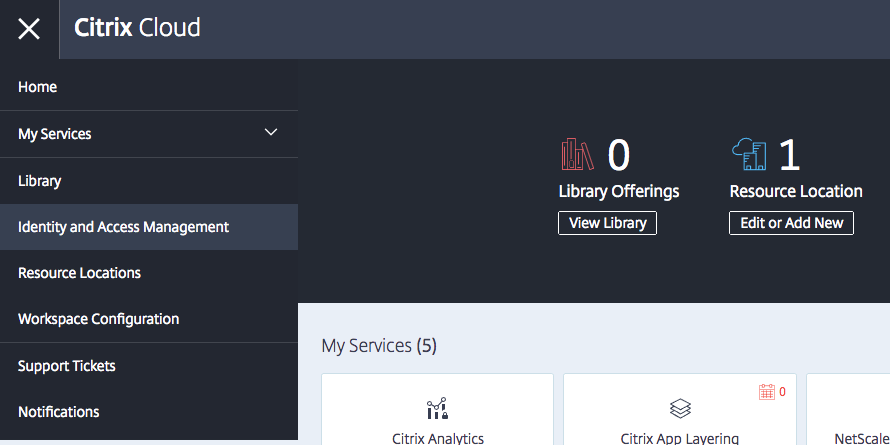
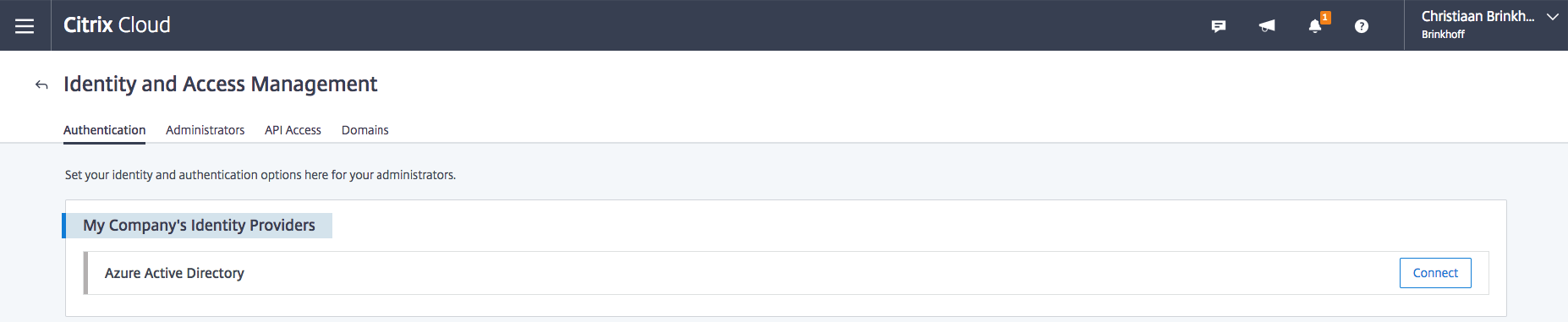
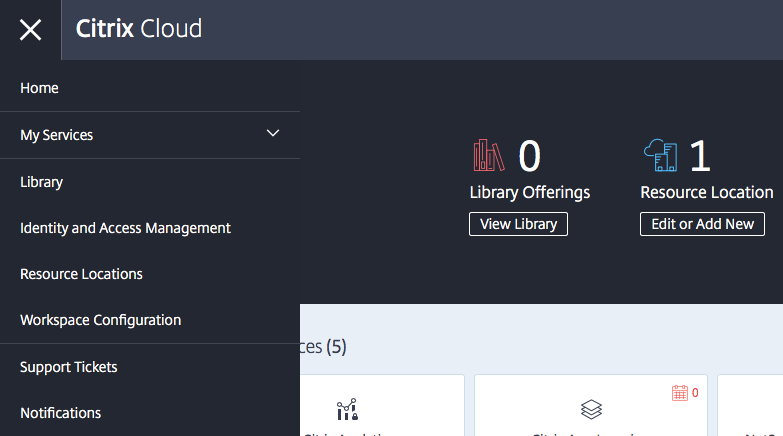
Open the Identity and Access Management option in the Hamburger (yes, I know… It’s called hamburger…) menu
Click on Connect
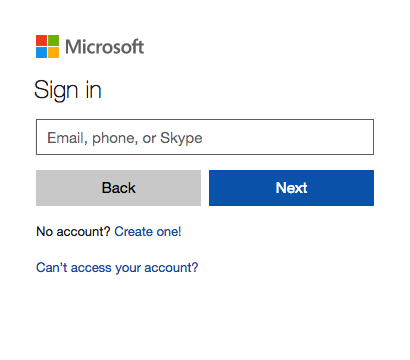
The portal will now redirect to the AzureAD Authentication portal
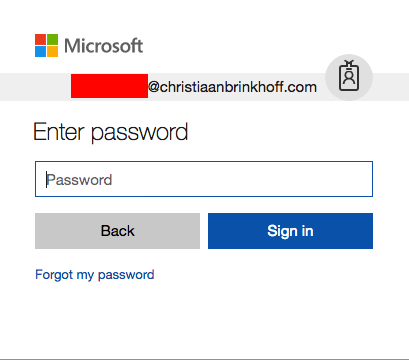
Logon with Azure Global Administrator credentials
Enter in the password and click on Sign in
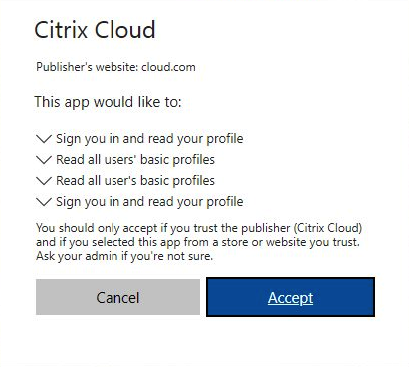
Accept the following rights request
Open the Workspace Configuration option in the Hamburger menu
Click on Authentication
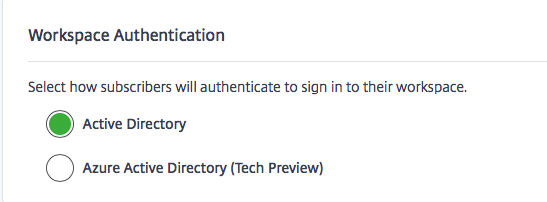
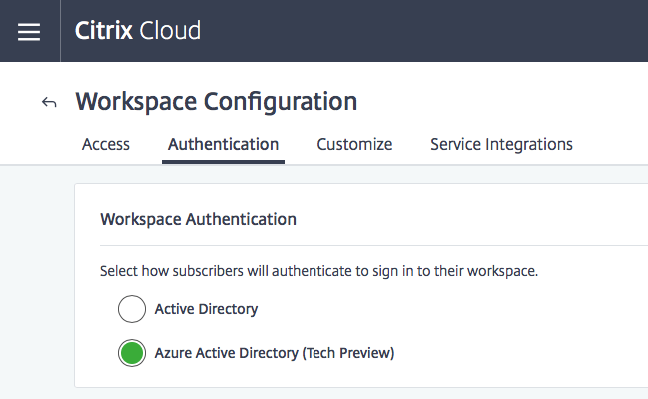
Click on Azure Active Directory (Tech Preview)
Accept the warning and click on Confirm
Confirm that the setting is on Azure Active Directory rather than (normal) Active Directory
Activate Azure Conditional Access – Trusted IPs whitelisting
In the following steps, I’ll explain how you could exclude the need for using Azure MFA for a separate network. This could be your company network, so you make sure that users only have to use MFA when they’re outside the company network. This is one of the settings that my users really appreciate… So how do you configure that? Continue reading…
Note: You’ll need Azure AD Premium or a Enterprise Mobility + Security ES License to use this feature!
Go (again) to the portal.azure.com website
Open Azure Active Directory
Open the Conditional Access menu
Click on Named Location followed by Configure MFA trusted IPs
The page will now redirect to the MFA authentication portal.
Go to the website -> http://www.whatsmyip.org
Copy the public IP and paste it in the trusted ips input field.
Also make sure to activate the Skip multi-factor authentication for request from federated users on my intranet.
Click on the Save button
The settings are now active!
Note: Need to know more about all the different conditions which you can set in Azure Conditional Access? Please read this Microsoft Docs article.
That’s it for now. I’ll hope to see you back soon.
Cheers,
Christiaan Brinkhoff